NIST CSF 2.0: The Ideal Standard for Establishing Basic Cybersecurity Rules for Legal Practitioners
2024/08/02
Jason Frocht
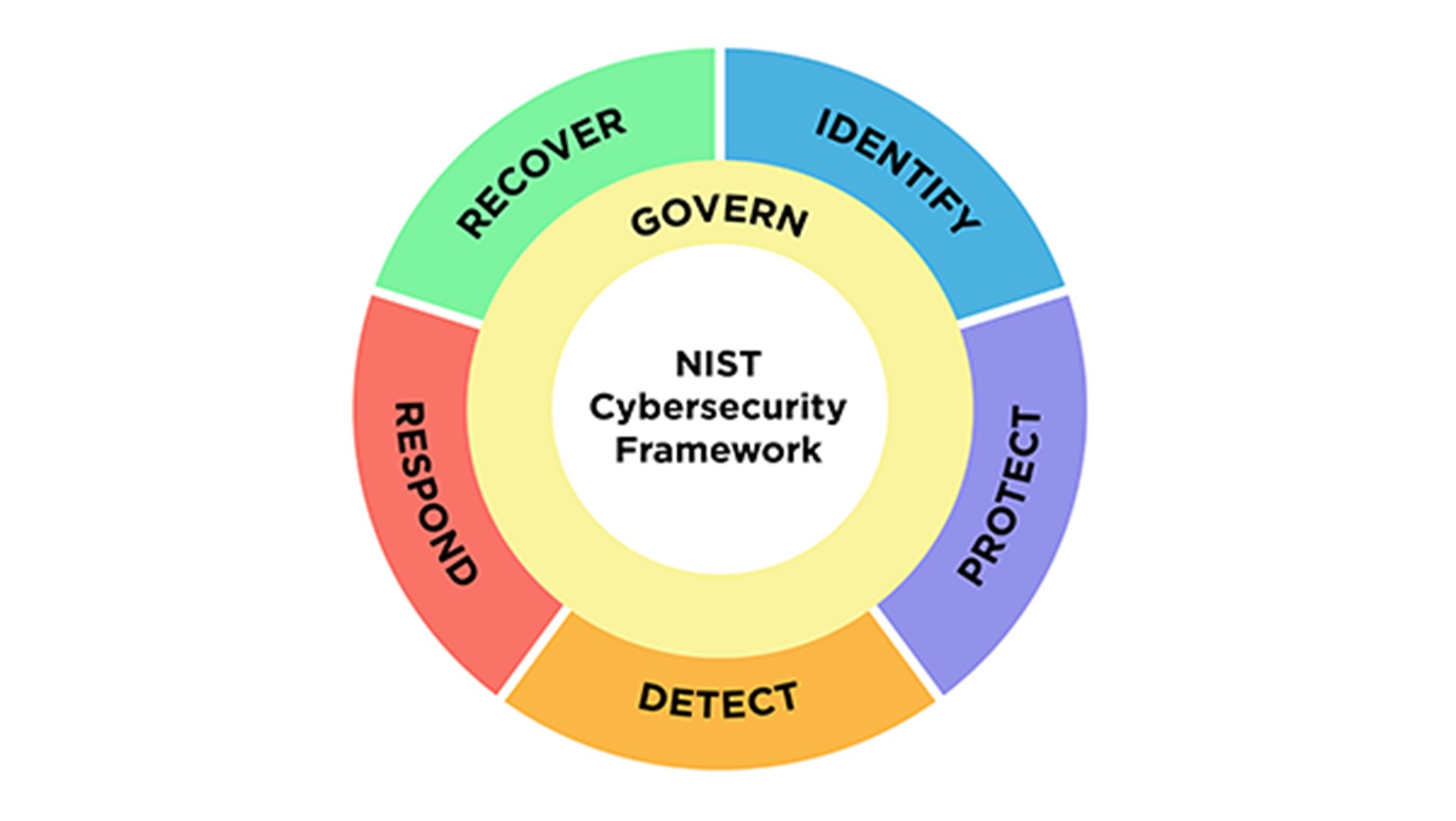
The National Institute of Standards and Technology developed its Cybersecurity Framework 2.0 and guides industry, government agencies, and other organizations to manage cybersecurity risks. This framework is ideal for an industry like the law where the transmission, interpretation, and collection of sensitive and private information is a matter of course. The cybersecurity framework (CSF) works to create a standard for both government agencies and industries to achieve their ideal cybersecurity risk outcomes and minimum guidance on practices and controls that could be used to achieve those outcomes.1 The center of NIST standards lies at the CSF Core, in comparison to NIST SP-800 which creates thorough standards for cybersecurity practitioners at all levels. The minimum standards in NIST 2.0 advise practical or rather reasonable methodologies for law firms. For example, NIST PR.PS-02 suggests that software is maintained, replaced, and removed commiserate with risk. In the case of prior analysis, software was not maintained commiserate with risk. There were security patches released addressing known security vulnerabilities that were not installed in a timely fashion. The lack of internal or external standards in this instance is what leads to the plethora of lawsuits—class action or otherwise—in addition to regulatory action against law firms for their failure to employ proper cybersecurity standards among their employees. The most important elements of the NIST standard are the CSF Core functions. These detail the broad requirements that firms need to take to protect themselves and their clients in modern digital transactions in the workplace. These requirements are built upon the five core functions: Govern, Identify, Protect, Detect, and Respond.
Govern: establishes the firm’s cybersecurity risk management strategy, expectations, and policy. For example, a state bar could set a firm’s floor for governance at the level of the instance of NIST PR.PS-02, and demand that firm software be updated or patched consistently every two months. Violations of this policy in the wake of a successful hacking event could lead to sanctions. This is a more extreme example, but sets cybersecurity policy amongst all firms in the state at the same base level.
Identify: establishes the function that law firms and their legal practitioners understand the current state of cybersecurity risks towards their organization. A state bar in this case could demand regular training in the same vein as a CLE. Such training could emphasize certain trends in cybersecurity threats, such as a rise or fall in phishing or spoofing attacks, or a new kind of attack based on weaknesses in the web infrastructure of commonly used online legal software.
Protect: the implementation of safeguards to protect a firm’s client data, including access control safeguards, data security technologies, and protective technologies. For example, when law firms establish either an in-house cybersecurity office or third-party cybersecurity provider, the floor for safeguards could include standardized patching requirements every 2 months, mandatory firmware updates at certain cyclical periods, and a mandatory training period on password security with rotating password renewal every few weeks.
Detect: the timely discovery of cybersecurity events to enable an appropriate response. For any legal practitioners, this could mean using a minimum standard of penetration testing regularly and stress testing of their systems for any potential network intrusions.
Respond: For any legal practitioners, an immediate plan of action should anticipate any response upon a potential attack on the firm’s systems, leakage of proprietary information, and most importantly, giving notice to clients. One of the advantages of creating a basic response threshold for firms is that there are already rules requiring mandatory disclosure of any leaks of substantial information including PII and proprietary information. In July 2023, the Securities and Exchange Commission (SEC) adopted rules requiring public companies to disclose all material cybersecurity incidents on a standard SEC form no later than four business days following the company’s determination that the incident was material.2 The Respond standard under NIST would simply extend this requirement to law firms that have been hacked leading to the same material leakage of client information. As firms are already involved in ongoing litigation regarding their failure to disclose hacking incidents (see above/add a reference to the Covington & Burling lawsuit later), the disclosure rules will act as an automatic safe harbor for law firms and protect them from litigious clients. As long as law firms and clients are on the same page regarding policies and procedures related to cybersecurity events, that notice shields legal practitioners from potential litigation for failure to respond.
Recover: Focuses on restoring capabilities or services that were impaired due to a cybersecurity incident. This function includes recovery planning, improvements, and communications to facilitate the recovery process. The recovery process will ensure that firms keep themselves in a position of maximum strength in their security posture and that they can effectively manage and give effective legal guidance to their clients going forward.
At the time of writing, there is no national, statutory, cross-sector minimum standard for information security, and there are especially no minimum standards of guidance or cybersecurity requirements for the legal profession in the United States. In the absence of such a minimum standard, CLR Technologies provides comprehensive cybersecurity services under the NIST 2.0 standard.
-
The NIST Cybersecurity Framework (CSF) 2.0, i. ↩︎
-
Reasonable Cybersecurity Guide at 74 (citing a new SEC requiring public companies to disclose all material cybersecurity incidents on a standard SEC form no later than four business days following the company’s determination that the incident was material). ↩︎